Custom Cloudflare WAF rules that every Drupal site should run
This blog post helps to summarise some of the default rules I will deploy to every Drupal (7 or 8) site as a base line.

Part of my day job is to help tune the Cloudflare WAF for several customers. This blog post helps to summarise some of the default rules I will deploy to every Drupal (7 or 8) site as a base line.
The format of the custom WAF rules in this blog post are YAML format (for humans to read), if you do want to create these rules via the API, then you will need them in JSON format (see the end of this blog post for a sample API command).
Default custom WAF rules
Unfriendly Drupal 7 URLs
I often see bots trying to hit URLs like /?q=node/add and /?q=user/register. This is the default unfriendly URL to hit on Drupal 7 to see if user registration or someone has messed up the permissions table (and you can create content as an anonymous user). Needless to say, these requests are rubbish and add no value to your site, let's block them.
description: 'Drupal 7 Unfriendly URLs (bots)'
action: block
filter:
expression: '(http.request.uri.query matches "q=user/register") or (http.request.uri.query matches "q=node/add")'Autodiscover
If your organisation has bought Microsoft Exchange, then likely your site will receive loads of requests (GET and POST) to which is likely to just tie up resources on your application server serving these 404s. I am yet to meet anyone that actually serves back real responses from a Drupal site for Autodiscover URLs. Blocking is a win here.
description: Autodiscover
action: block
filter:
expression: '(http.request.uri.path matches "/autodiscover\.xml$") or (http.request.uri.path matches "/autodiscover\.src/")'Wordpress
Seeing as Wordpress has a huge market share (34% of all websites) a lot of Drupal sites get caught up in the mindless (and endless) crawling. These rules will effectively remove all of this traffic from your site.
description: 'Wordpress PHP scripts'
action: block
filter:
expression: '(http.request.uri.path matches "/wp-.*\.php$")'description: 'Wordpress common folders (excluding content)'
action: block
filter:
expression: '(http.request.uri.path matches "/wp-(admin|includes|json)/")'I separate wp-content into it's own rule as you may want to disable this rule if you are migrating from a old Wordpress site (and want to put in place redirects for instance).
description: 'Wordpress content folder'
action: block
filter:
expression: '(http.request.uri.path matches "/wp-content/")'SQLi
I have seen several instanced in the past where obvious SQLi was being attempted and the default WAF rules by Cloudflare were not intercepting them. This custom WAF rule is an attempt to fill in this gap.
description: 'SQLi in URL'
action: block
filter:
expression: '(http.request.uri.path contains "select unhex") or (http.request.uri.path contains "select name_const") or (http.request.uri.path contains "unhex(hex(version()))") or (http.request.uri.path contains "union select") or (http.request.uri.path contains "select concat")'Drupal 8 install script
Drupal 8's default install script will expose your major, minor and patch version of Drupal you are running. This is bad for a lot of reasons.
It is better to just remove these requests from your Drupal site altogether. Note, this is not a replacement for upgrading Drupal, it is just to make fingerprinting a little harder.
description: 'Install script'
action: block
filter:
expression: '(http.request.uri.path eq "/core/install.php")'Microsoft Office and Skype for Business
Microsoft sure is good at making lots of products that attempt to DoS its own customers websites. These requests are always POST requests, often to your homepage, and you require partial string matching to match the user agent, as it changes with the version of Office/Skype you are running.
In large organisation, I have seen the number of requests here number in the hundreds of thousands per day.
description: 'Microsoft Office/Skype for Business POST requests'
action: block
filter:
expression: '(http.request.method eq "POST") and (http.user_agent matches "Microsoft Office" or http.user_agent matches "Skype for Business")'Microsoft ActiveSync
Yet another Microsoft product that you don't why it is trying to hit another magic endpoint that doesn't exist.
description: 'Microsoft Active Sync'
action: block
filter:
expression: '(http.request.uri.path eq "/Microsoft-Server-ActiveSync")'Using the Cloudflare API to import custom WAF rules
It can be a pain to have to manually point and click a few hundred times per zone to import the above rules. Instead you would be better off to use the API. Here is a sample cURL command you can use do import all of the above rules in one easy go.
You will need to replace the redacted sections with your details.
curl 'https://api.cloudflare.com/client/v4/zones/XXXXXXXXXXXXXX/firewall/rules' \
-H 'X-Auth-Email: XXXXXXXXXXXXXX' \
-H 'X-Auth-Key: XXXXXXXXXXXXXX'
-H 'Accept: application/json' \
-H 'Content-Type: application/json'
-H 'Accept-Encoding: gzip'
-X POST \
-d '[{"ref":"","description":"Autodiscover","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.path matches \"\/autodiscover\\.xml$\") or (http.request.uri.path matches \"\/autodiscover\\.src\/\")"}},{"ref":"","description":"Drupal 7 Unfriendly URLs (bots)","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.query matches \"q=user\/register\") or (http.request.uri.query matches \"q=node\/add\")"}},{"ref":"","description":"Install script","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.path eq \"\/core\/install.php\")"}},{"ref":"","description":"Microsoft Active Sync","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.path eq \"\/Microsoft-Server-ActiveSync\")"}},{"ref":"","description":"Microsoft Office\/Skype for Business POST requests","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.method eq \"POST\") and (http.user_agent matches \"Microsoft Office\" or http.user_agent matches \"Skype for Business\")"}},{"ref":"","description":"SQLi in URL","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.path contains \"select unhex\") or (http.request.uri.path contains \"select name_const\") or (http.request.uri.path contains \"unhex(hex(version()))\") or (http.request.uri.path contains \"union select\") or (http.request.uri.path contains \"select concat\")"}},{"ref":"","description":"Wordpress common folders (excluding content)","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.path matches \"\/wp-(admin|includes|json)\/\")"}},{"ref":"","description":"Wordpress content folder","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.path matches \"\/wp-content\/\")"}},{"ref":"","description":"Wordpress PHP scripts","paused":false,"action":"block","priority":null,"filter":{"expression":"(http.request.uri.path matches \"\/wp-.*\\.php$\")"}}]'How do you know the above rules are working
Visit the firewall overview tab in Cloudflare's UI to see how many requests are being intercepted by the above rules.
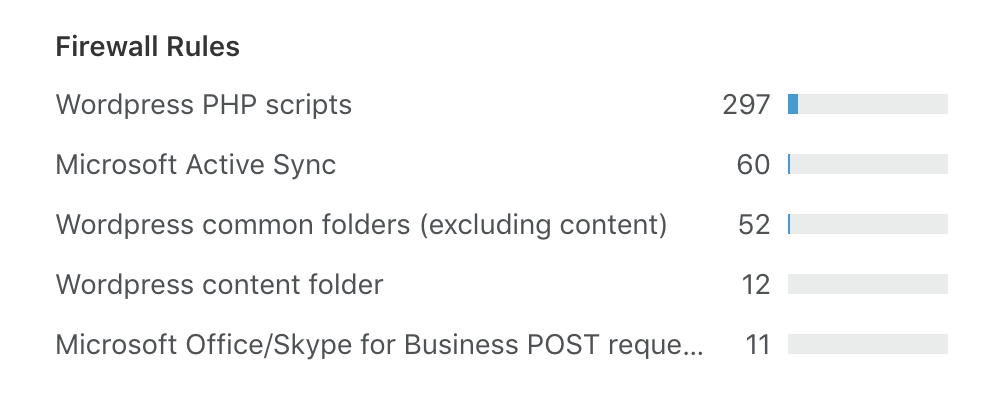
Final thoughts
The above custom WAF rules are likely not the only custom WAF rules you will need for any given Drupal site, but it should at least be a good start. Let me know in the comments if you have any custom WAF rules that you always deploy. I would be keen to update this blog post with additional rules from the community.
This is likely the first post in a series of blog posts on customising Cloudflare to suit your Drupal site. If you want to stay up to date - subscribe to the RSS feed, sign up for email updates, or follow us on Twitter.
